
G2 Rating
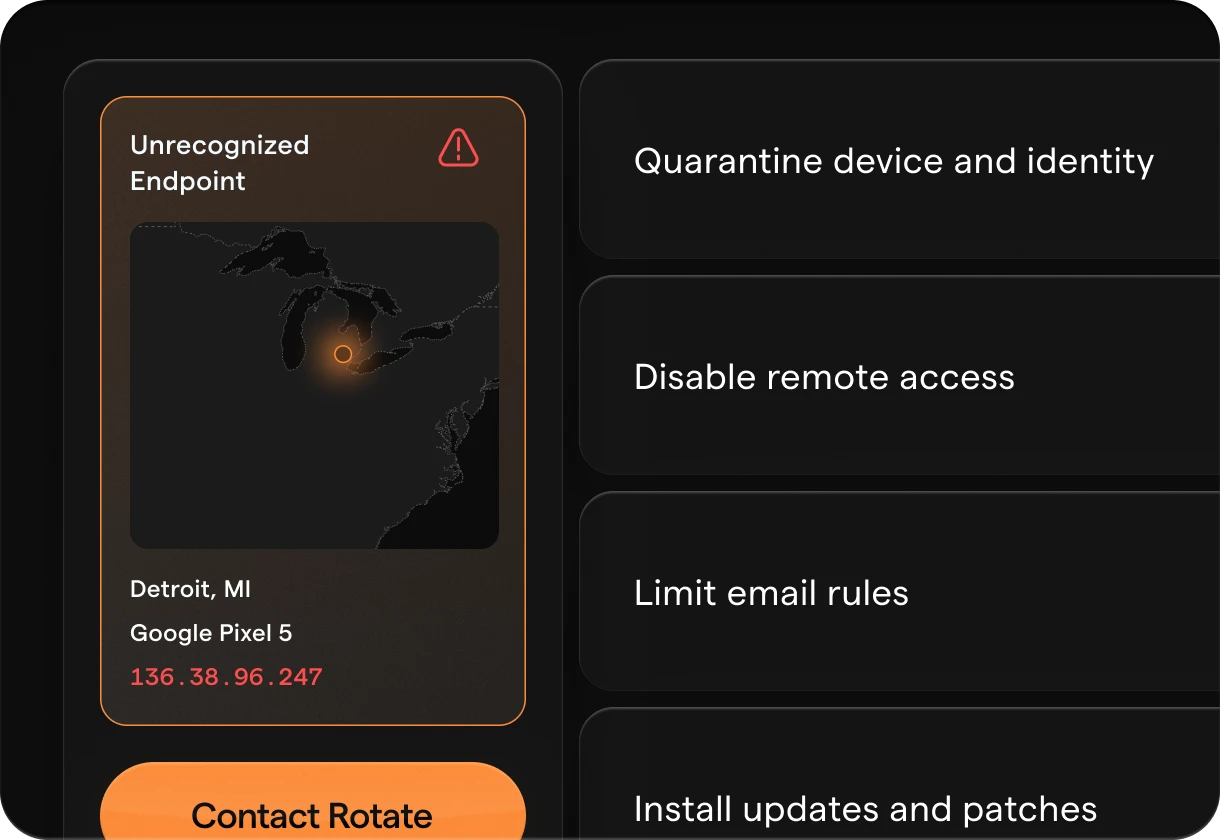
Unrecognized Endpoint
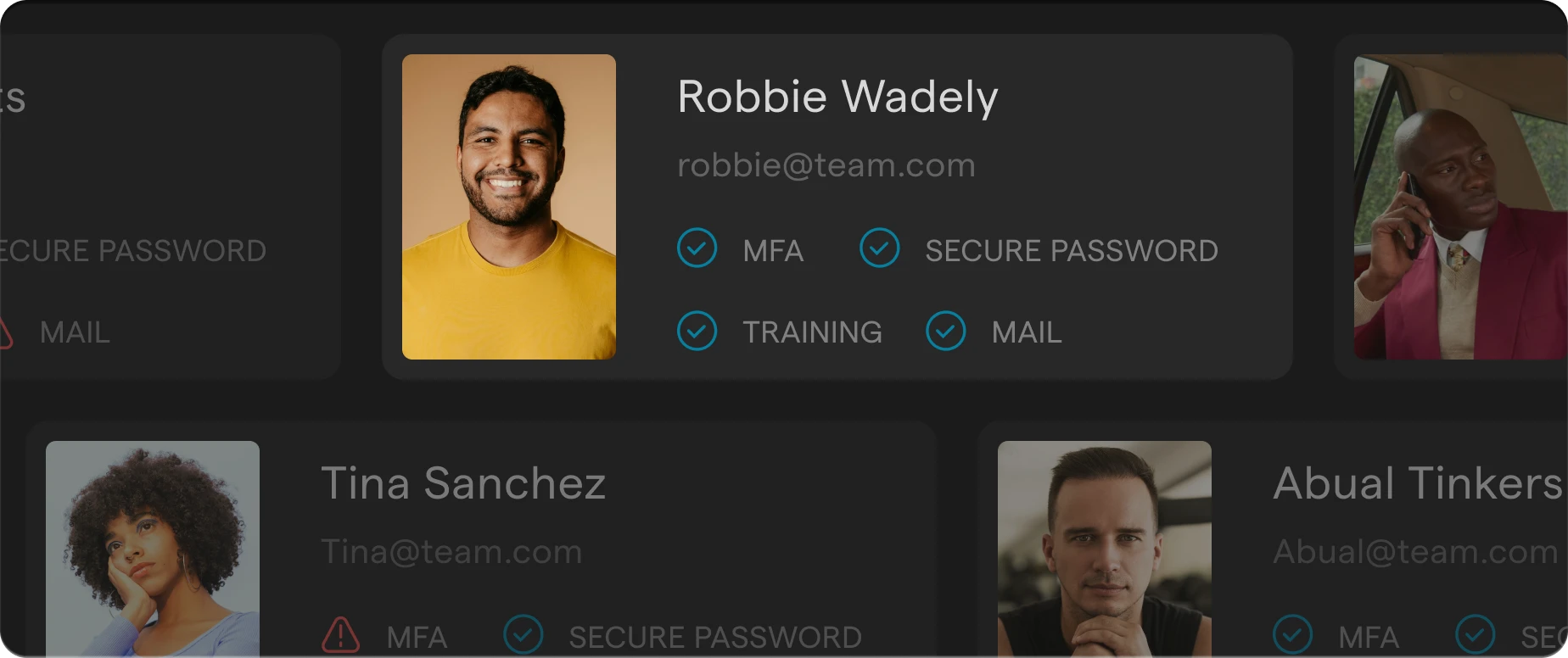
Enforce MFA Login
New York City, NY
MacBook Pro
123.38.96.247
Malware Detection
Took Device Offline
Salt Lake City, UT
Google Pixel 5
136.38.96.247
Email Phishing Attempt
Deleted & Blocked Sender
Paris, FR
iPad Air
541.38.96.247
Unapproved Network
Flag User and Device
Mexico City, MEX
Surface Go 3
984.38.96.247
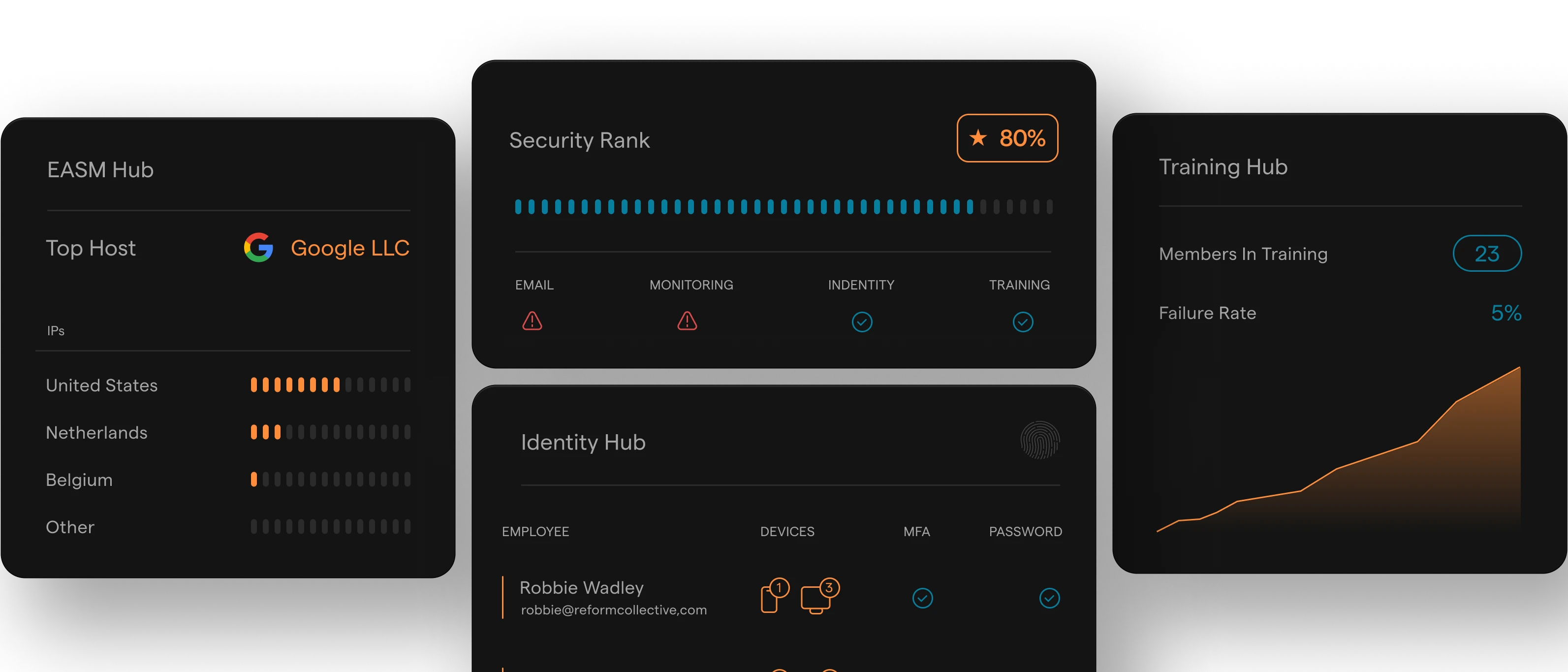
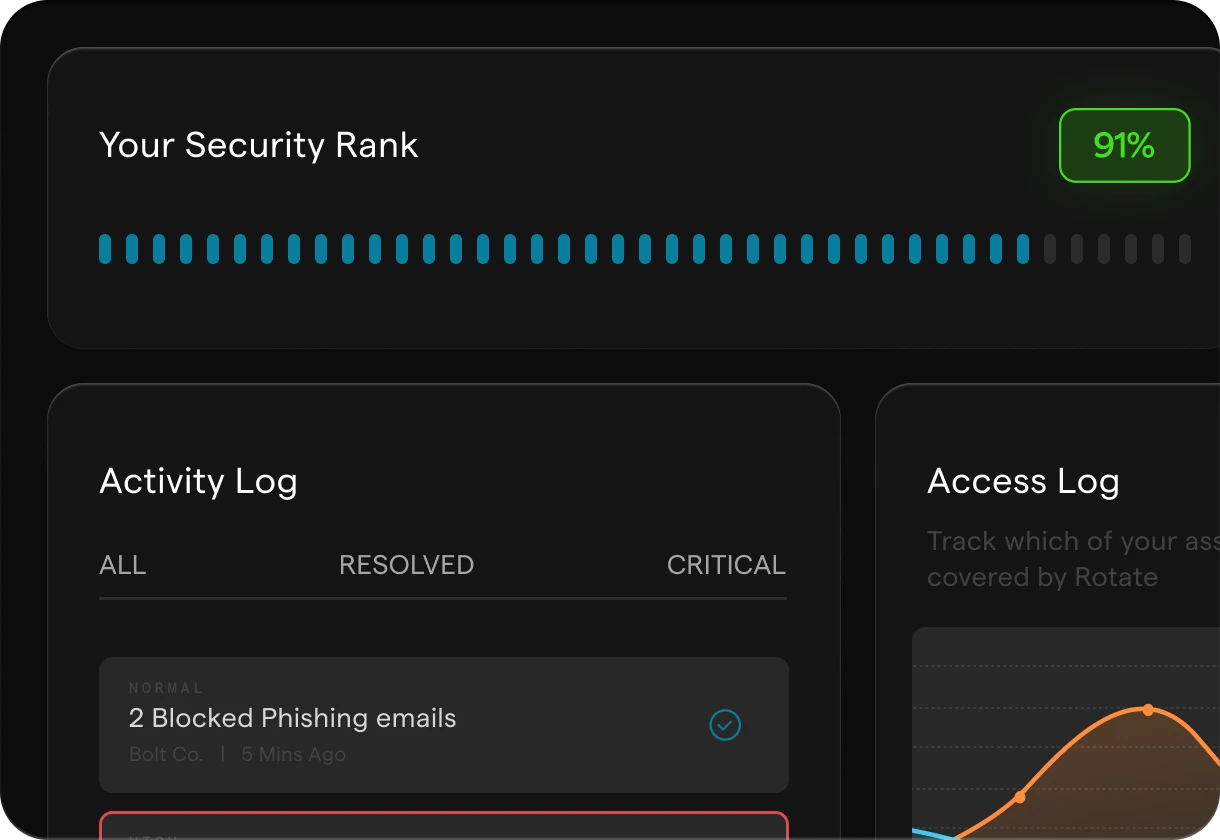
Across Every Layer.
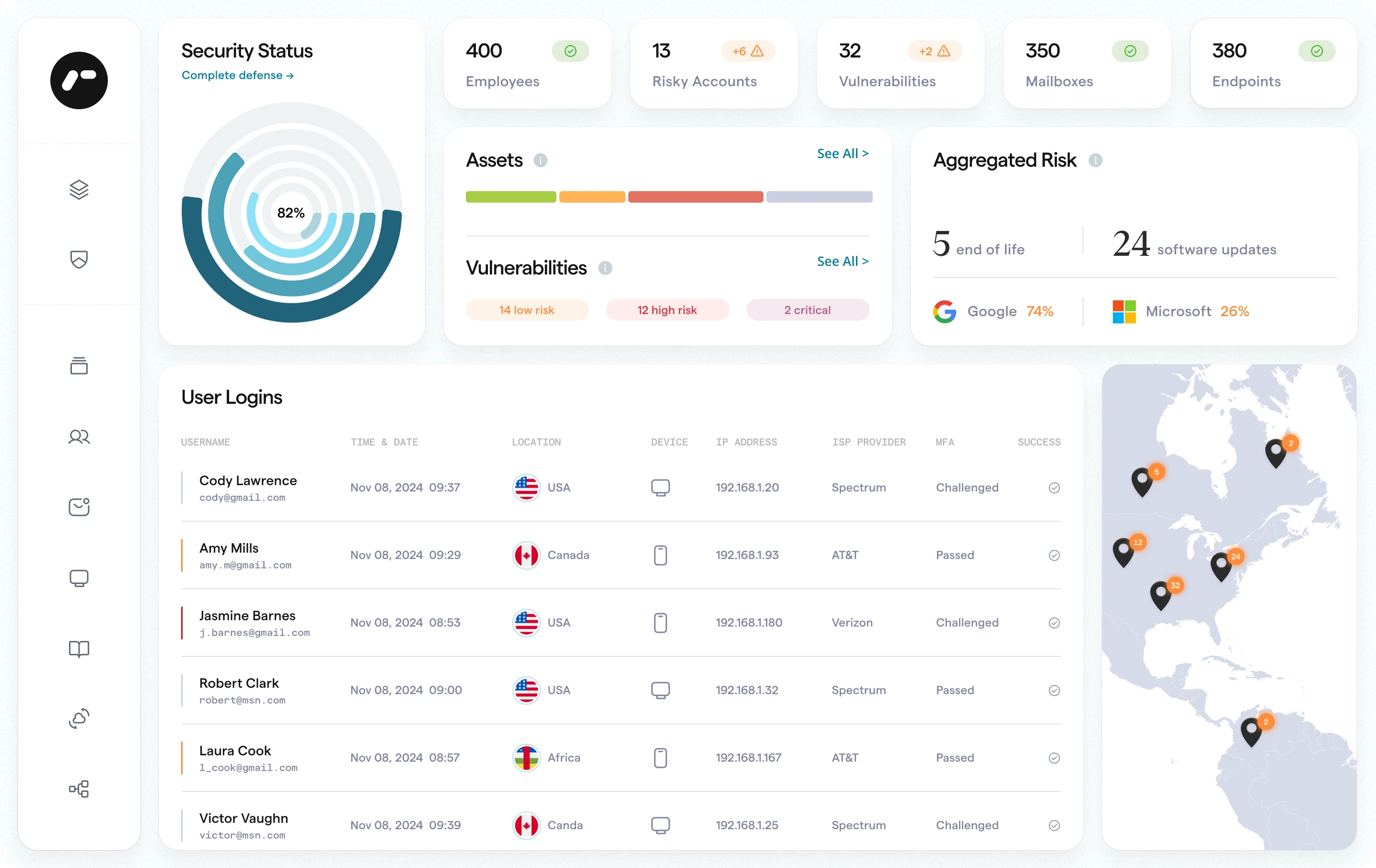
Proven AI-driven protection across users, emails, devices, apps, and external assets.
Rotate detects and stops threats in real time, phishing, ransomware, credential leaks, and more. With centralized control and seamless integrations, security teams gain full visibility and faster response across the entire environment.
Platform Overview

Identity Hub
Identity protection with strong MFA enforcement, rapid anomaly detection, password monitoring, data leak alerts, and account takeover protection.

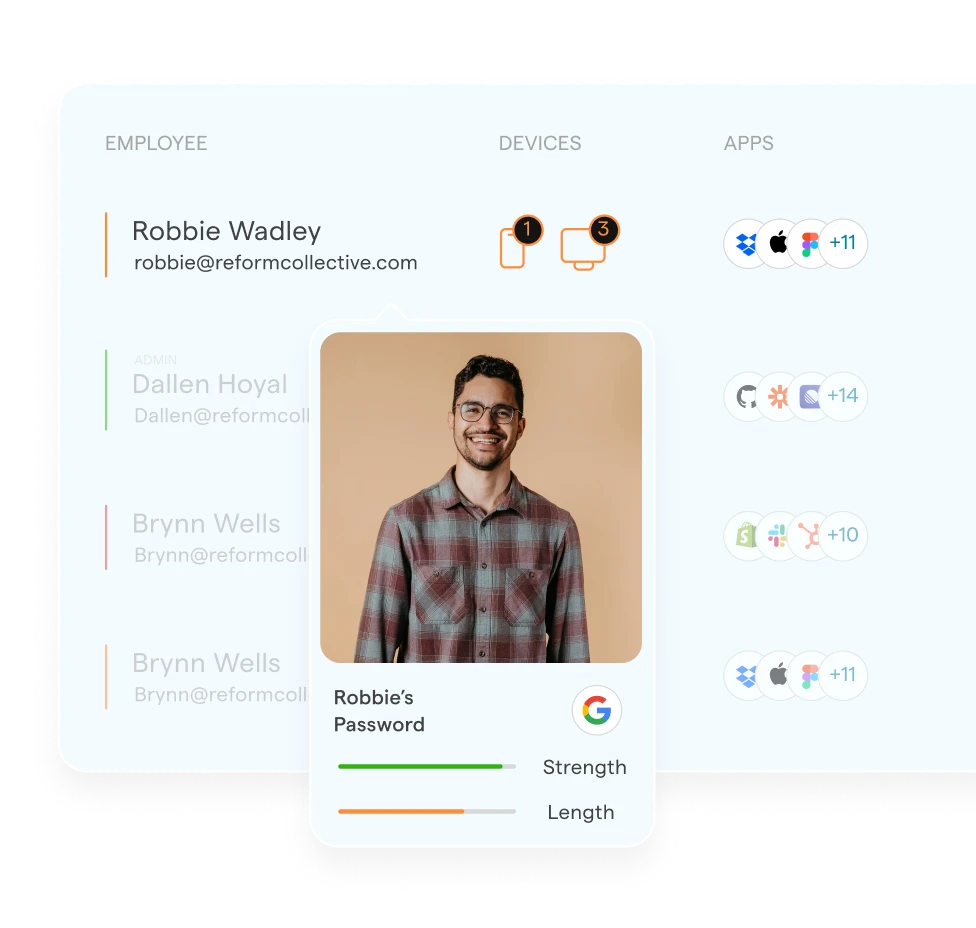
More about Identity Hub
Email Hub
Protection against phishing, fraud, and spoofing with email posture checks. Works with Google, Microsoft. Built to stop threats before they reach the inbox.

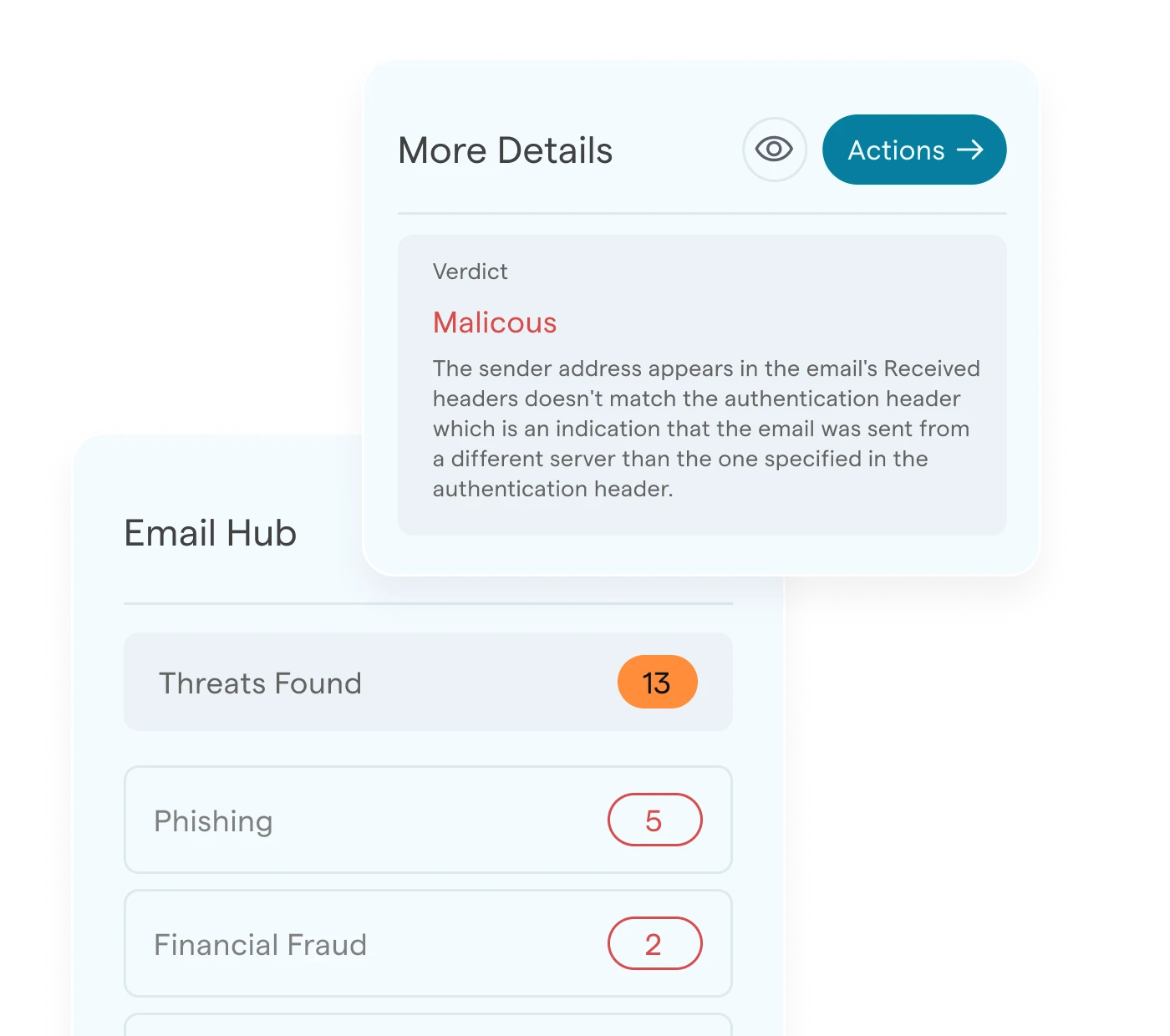
More about Email Hub
Endpoint Hub
Device protection with full fleet visibility, compliance monitoring, and insights into antivirus, apps, and more. Integrated with your endpoint tools.

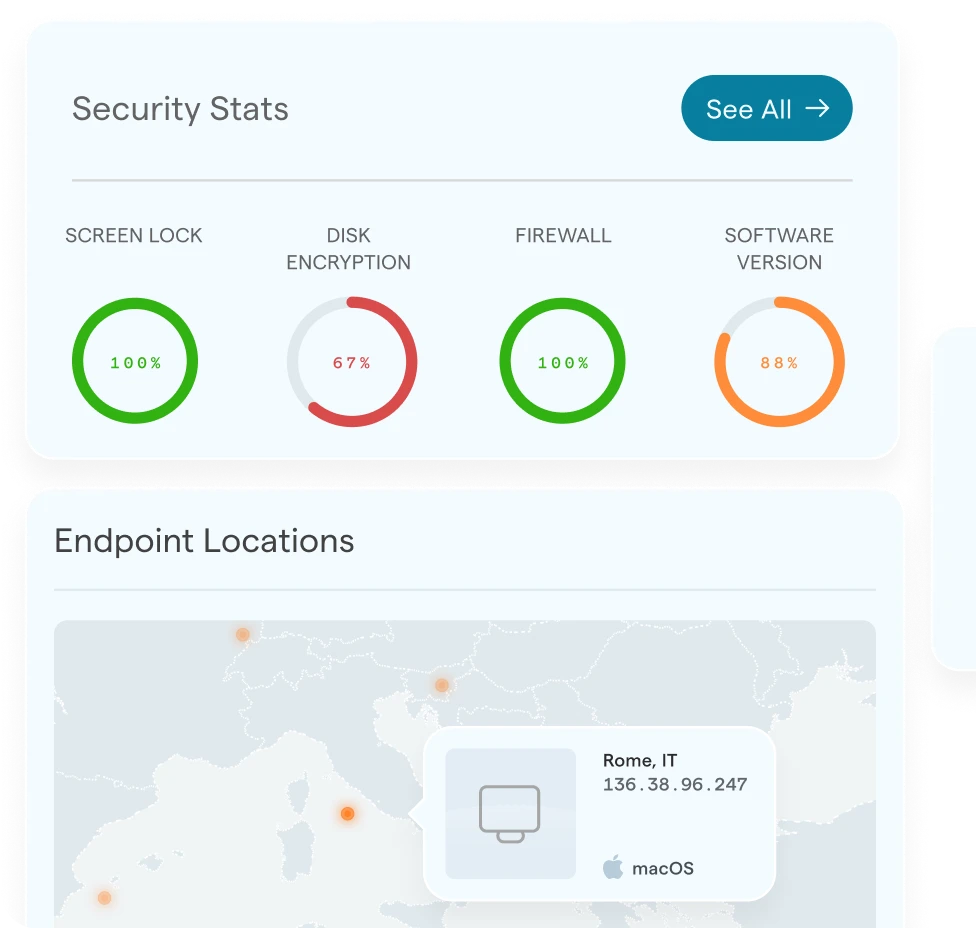
More about Endpoint Hub
Data Hub
Data Loss Protection against leaks, with continuous monitoring, permission control, and sensitive data classification.

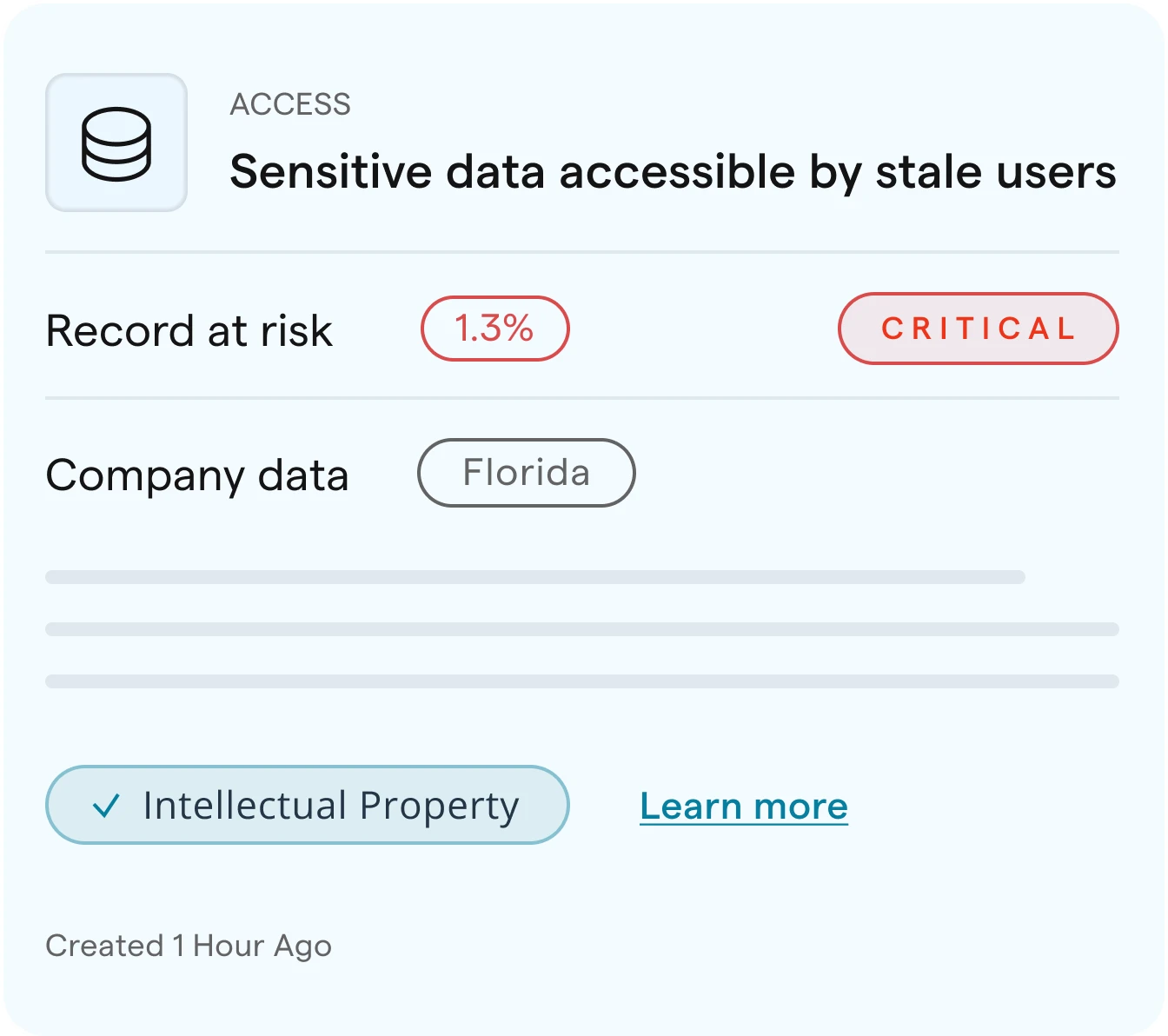
More about Data Hub
Training Hub
Train employees with real-world simulations and built-in programs. Stay compliant with out-of-the-box content and track progress with insights.

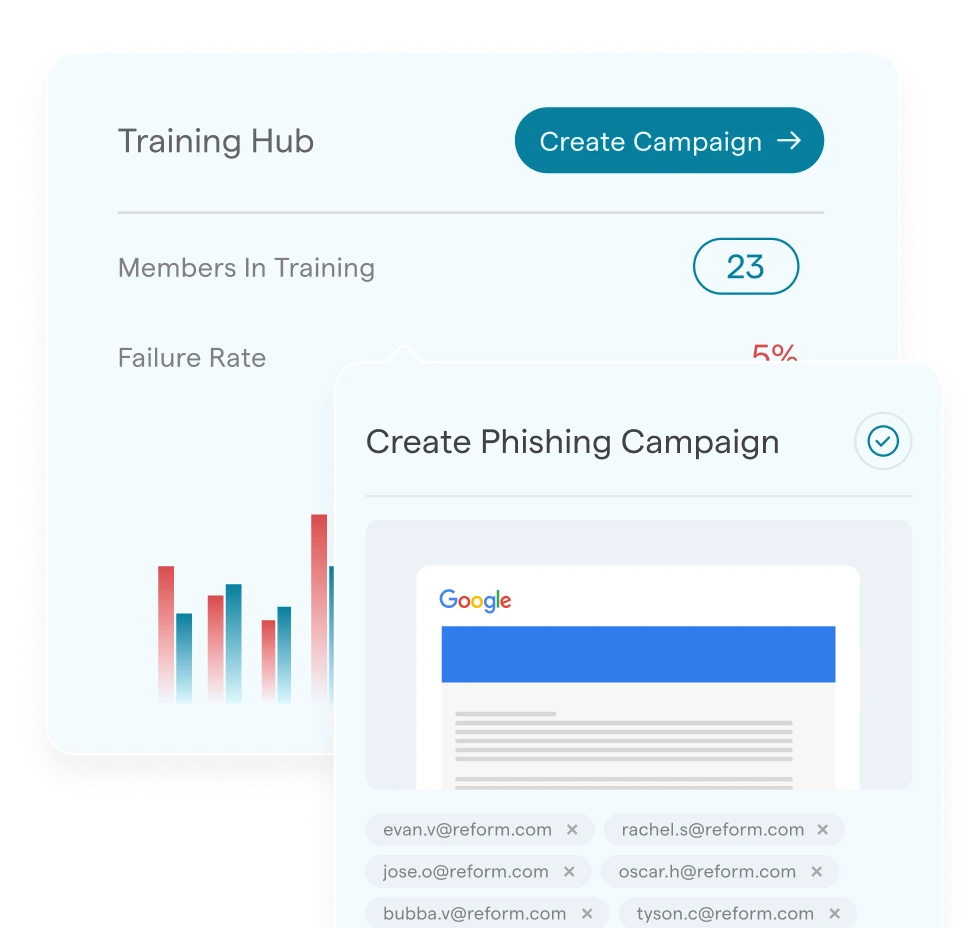
More about Training Hub
EASM Hub
Track external risks with threat intelligence, dark web monitoring, and vulnerability insights across cloud assets and domains.

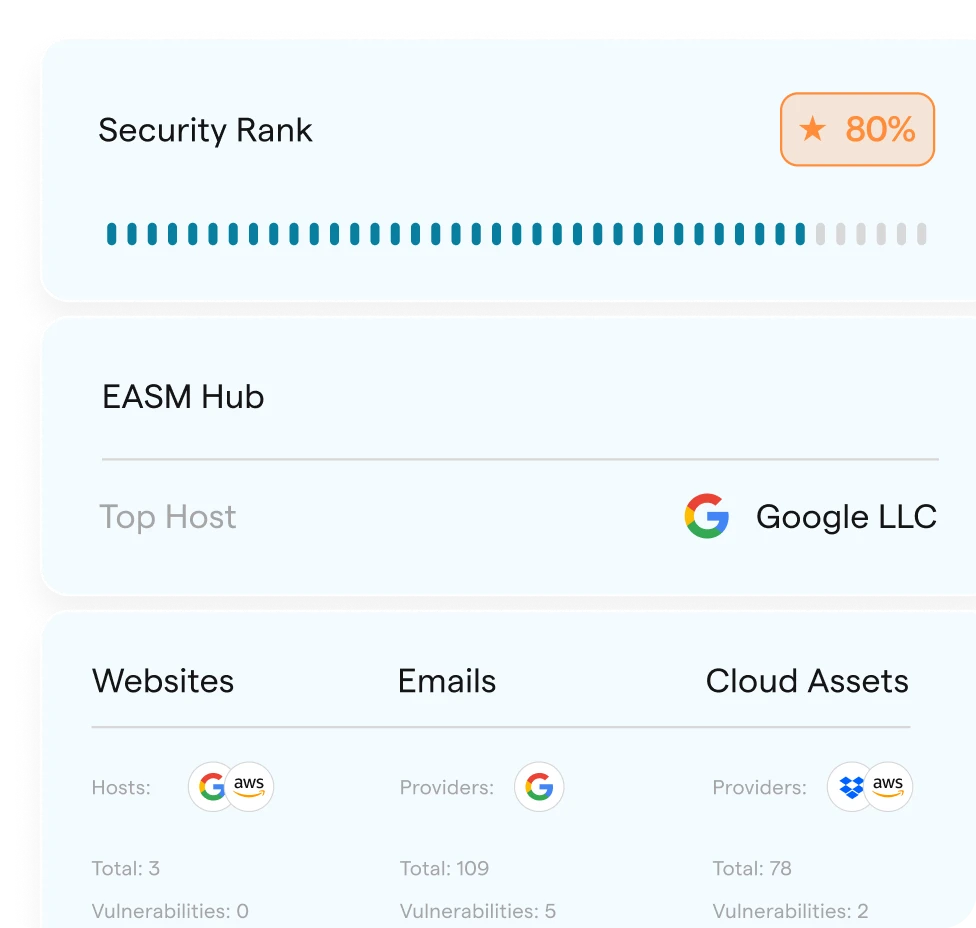
More about EASM Hub
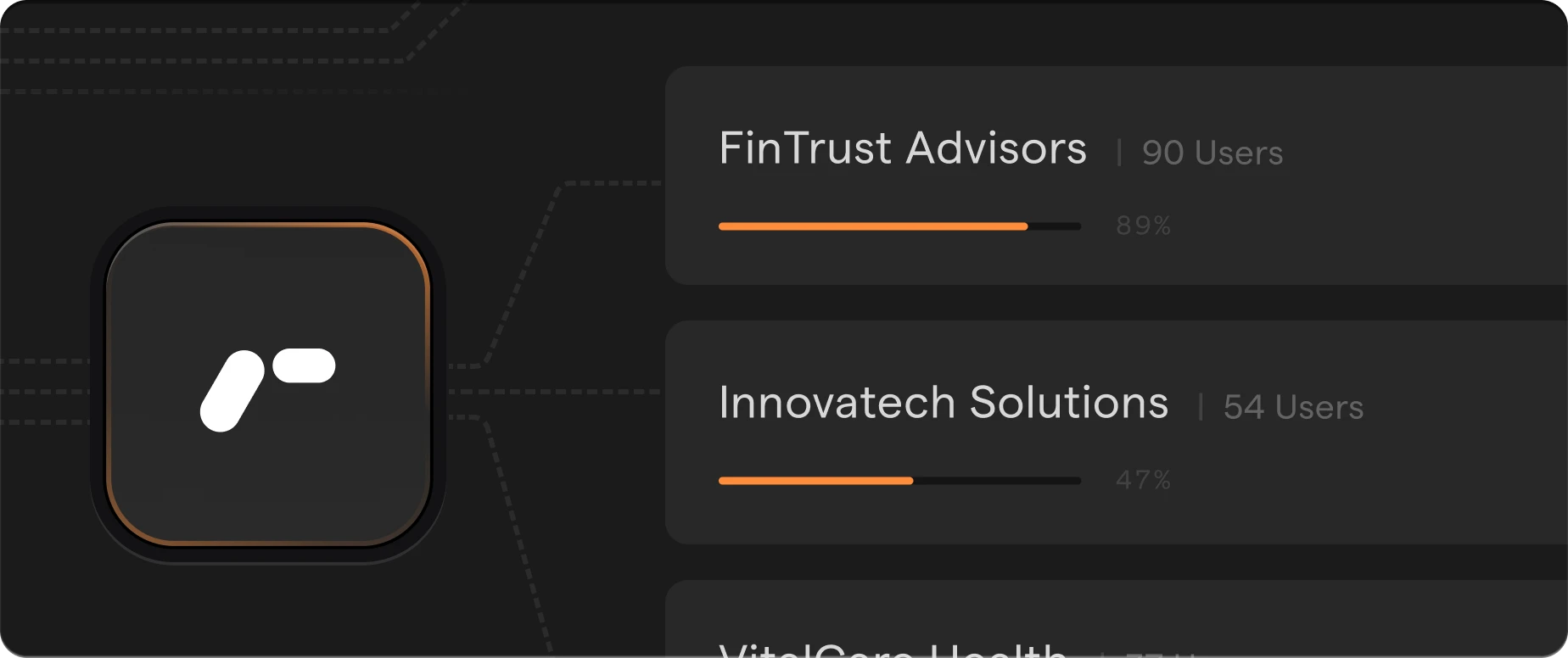
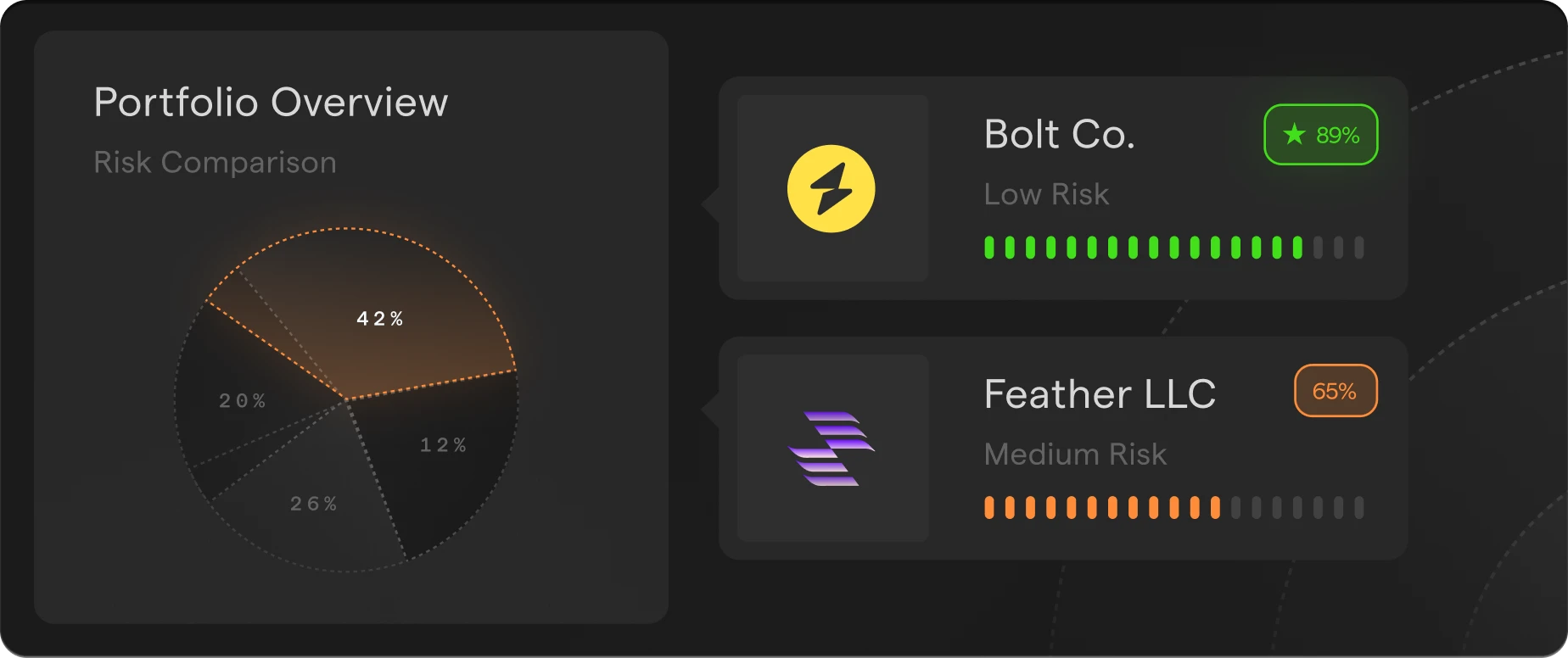
Managed Detection & Response
24/7 detection, investigation, and response powered by AI, with expert guidance and centralized visibility across your organization.








Over
90%
of businesses aretargeted
bya
cybersecurity attack at leastonce
a
year.
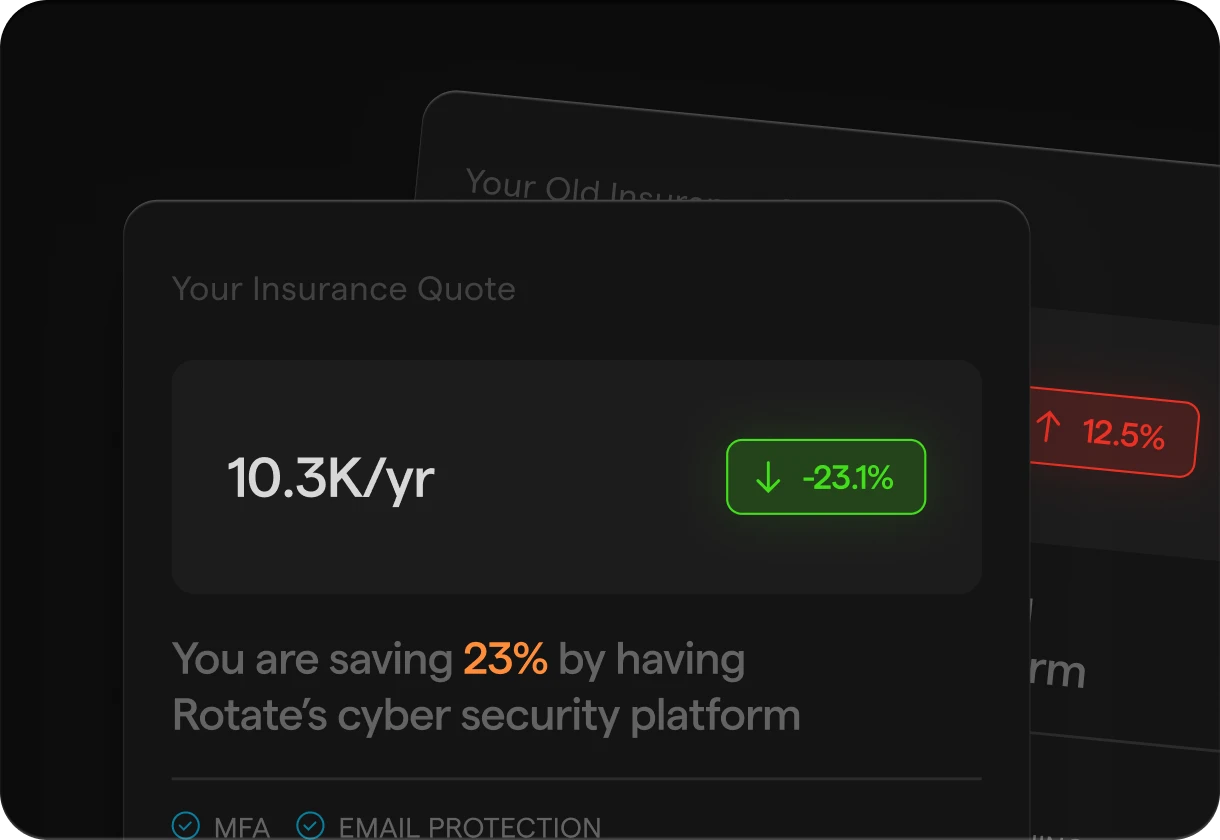
$1.85
million
is theaverage
cost
to remediate a cybersecurity attack.
66%
of companies that are victims of ransomware attacksgo
bankrupt.

It’s never been more critical to deploy the right cybersecurity platform.
Get started today and secure your company.