The Rotate
Compliance & Security
Built-in controls that check all the boxes.
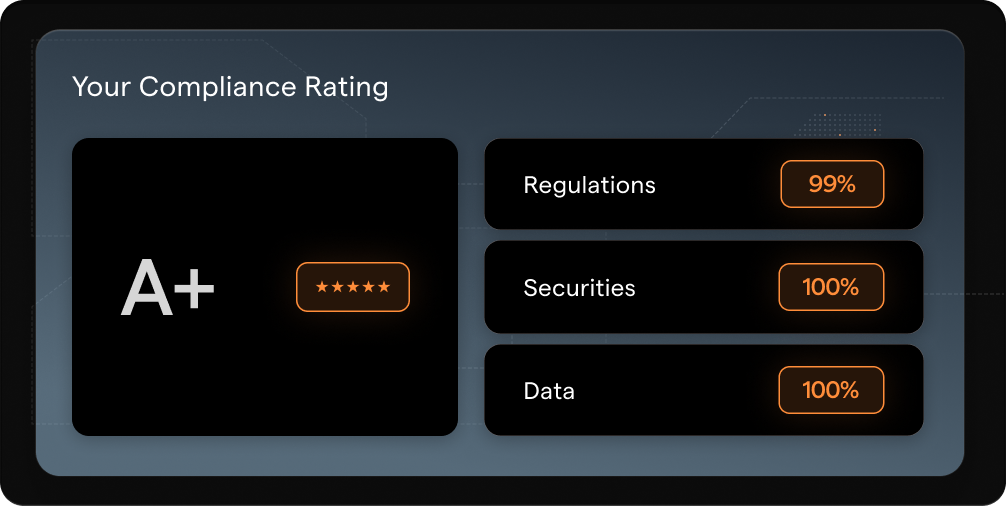
Get real-time proof of security readiness with trusted
protection across users, devices, emails, and more.
Get real-time proof of security readiness with trusted
protection across users, devices, emails, and more.
Built-In Protection
Compliance without complexity
Rotate helps you align with leading frameworks like ISO 27001, SOC 2, and NIST.
From MFA and phishing defense to device and
email security, every layer is built to support audit readiness and continuous compliance.
Forget spreadsheets and patchwork tools.
Rotate connects the dots across your environment, automates evidence collection, and simplifies reporting - all in one platform.
Compliance Built In.
Security Built Right.
Security Built Right.
Rotate automates the security controls required for compliance with SOC 2,
HIPAA, ISO 27001, GDPR, and more, backed by real-time visibility and proof.
HIPAA, ISO 27001, GDPR, and more, backed by real-time visibility and proof.
No manual checklists. No complex integrations. Just everything you need to show
your organization is secure, prepared, and audit-ready.
your organization is secure, prepared, and audit-ready.
Identity-First Security
MFA, SSO, and password policies enforced across all users - with full access logs to prove it.
Employee Training
Run phishing simulations and awareness training programs that meet key compliance standards.
Device Visibility
Ensure every workstation meets requirements with automated checks and alerts.
Live Reporting
Dashboards show real-time status across users, devices, and training.
Access Oversight
Track user roles and privileges, and enforce least-privilege access.
Quick Onboarding
Deploy in minutes with SSO. No complex setup or integrations needed.
Compliance Across
Every Control
Every Control

From identity to endpoints, Rotate continuously enforces the security layers auditors care about most - and lets you prove it at any time.
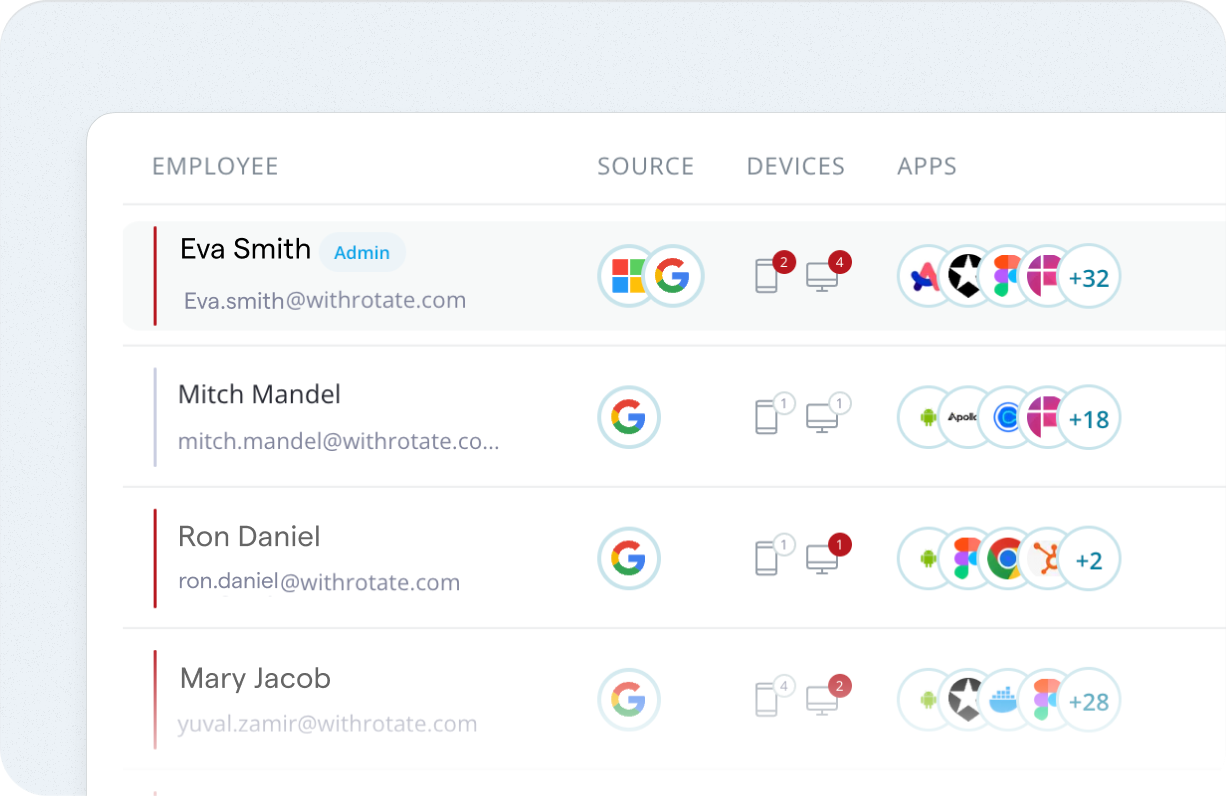
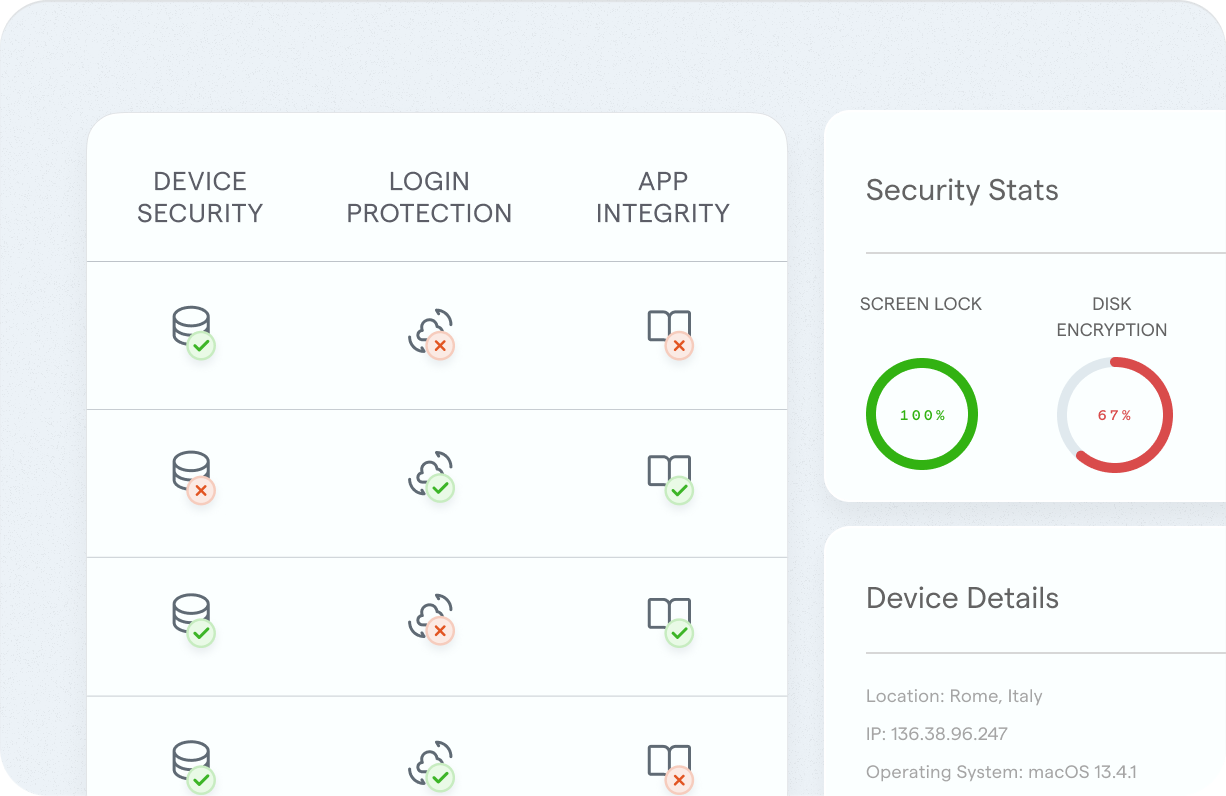
Device Compliance Monitoring
Ensure every laptop and workstation meets compliance requirements. Rotate continuously checks for encryption, OS updates, and risky behavior, and lets you respond quickly when a device falls out of line.
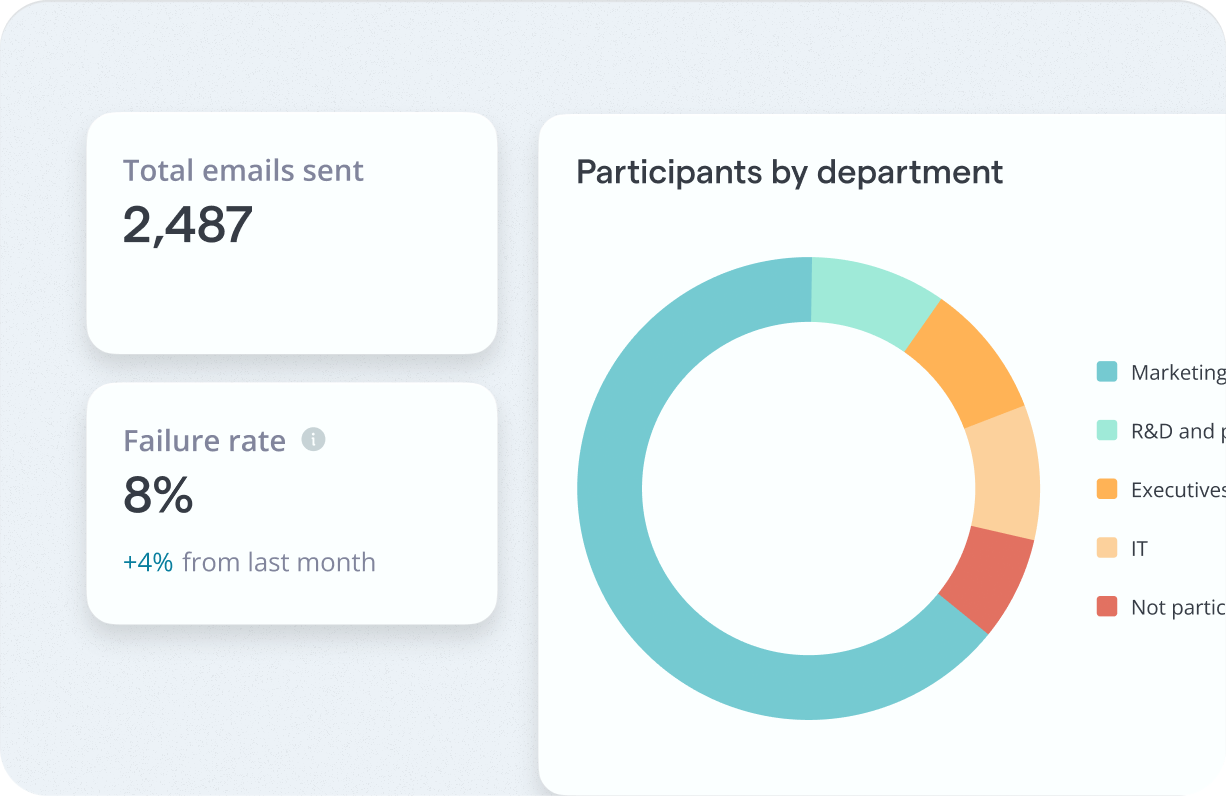
Training Compliance Tracking
Rotate automatically enrolls employees in phishing simulations and awareness training, ensuring your workforce stays compliant year-round. You get real-time progress, risk insights, and exportable reports, all ready for your next audit.
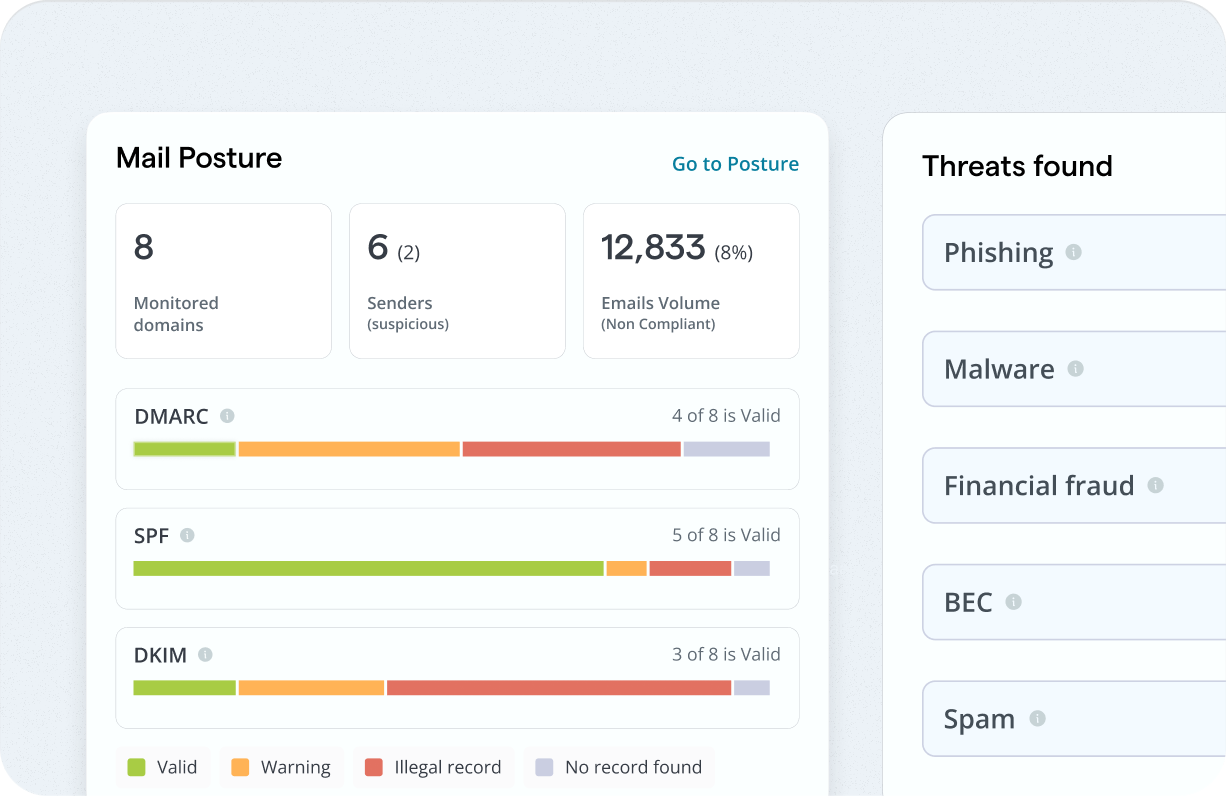
Live Audit Reporting
Skip the spreadsheets and static checklists. Rotate automatically collects evidence across users, devices, and policies - so you're always one step ahead when it’s time to prove compliance.
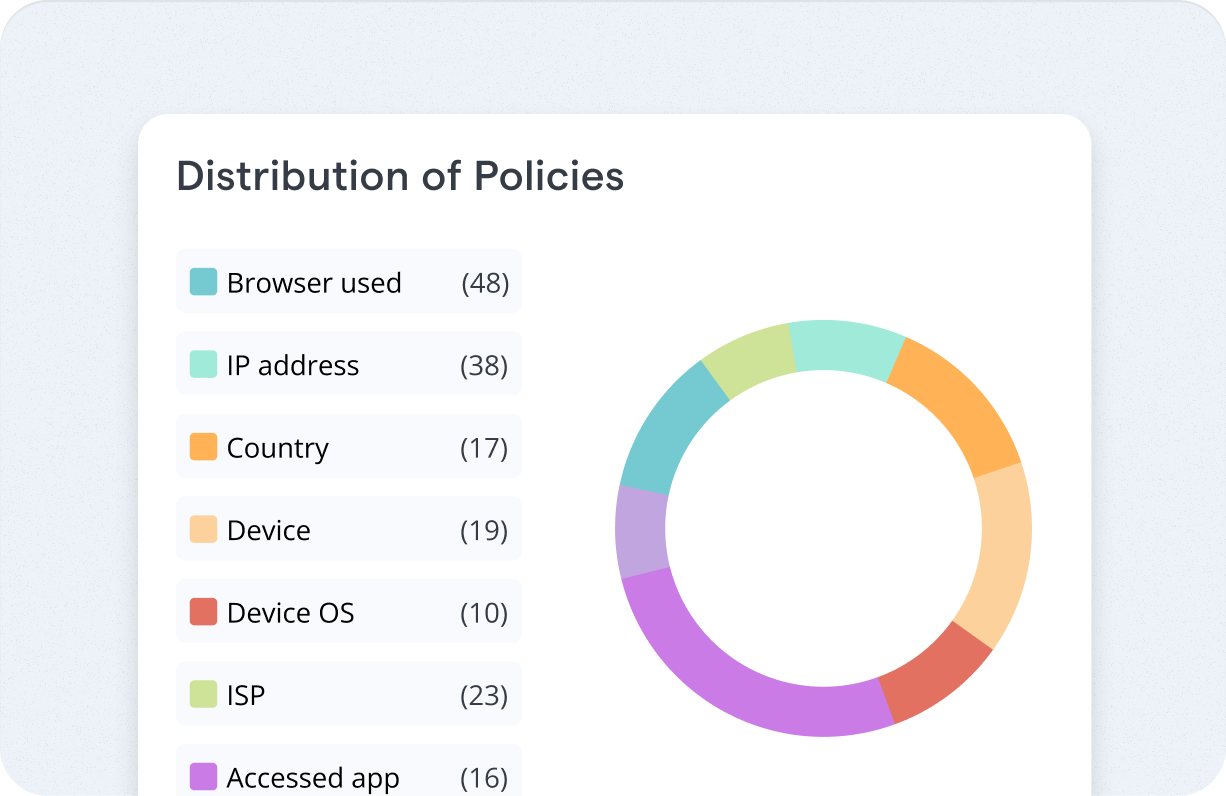
Email Security Controls
Protect email environments and meet compliance needs. Rotate monitors for hidden threats like malicious rules or forwarding, giving you fast, compliant tools to block or reset compromised accounts.
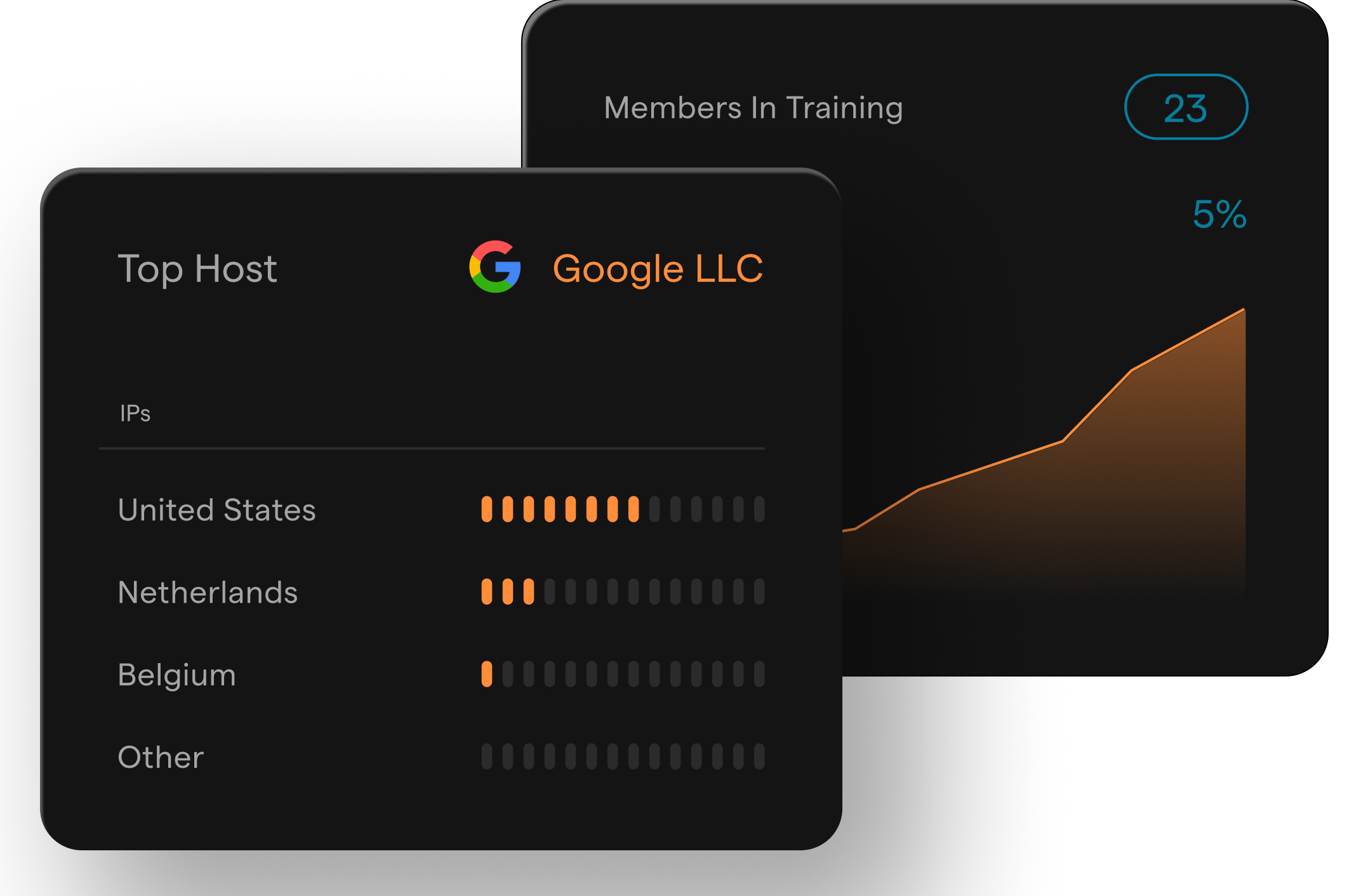
Identity & Access Enforcement
Track login activity, detect risky sign-ins, and enforce MFA and password policies - all from a unified dashboard. Rotate gives you full visibility into access behavior, with logs and controls mapped to major compliance standards.
Right Out
of the Box
of the Box
01
Simplicity -
Rotate eliminates the complexity of other systems and consolidates defenses in one platform.02
Speed -
From fast onboarding to continuous monitoring, Rotate is built for hit-the-ground-running deployment without fear of future slowdowns.03
Coverage -
Every layer is monitored - users, devices, email, and apps. Rotate gives you end-to-end visibility and context for every compliance requirement.04
Proof -
Auditors love clarity. Rotate continuously collects and organizes the evidence you need to demonstrate compliance with confidence.Data on Cyber Threats
30%Reduction in time to reach compliance
50%Savings on compliance-related spend
x2Improved certification results using the same controls
Customer Stories
Proven Results from Trusted Partners
How Rotate makes your digital world safer.

We avoided a wire fraud thanks to Rotate’s policy enforcement and clear investigation tools - exactly what our auditors look for.



