
Robust protection across all digital assets
See how we make world-class cybersecurity fast and seamless.
Request demo
Get the protection you need, where and when you need it
Rotate's modular hub system provides comprehensive protection against a host of sophisticated cyber threats.
Extended Detection and Response
Powered by AI, consolidates and centralizes monitoring and analysis data across all hubs, enabling real-time threat aggregation in one place. Additionally, it provides automatic remediation for any identified issues.


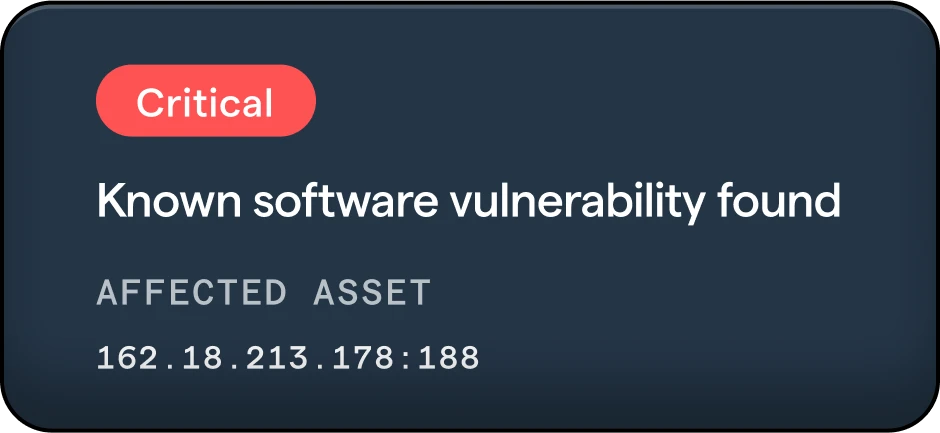
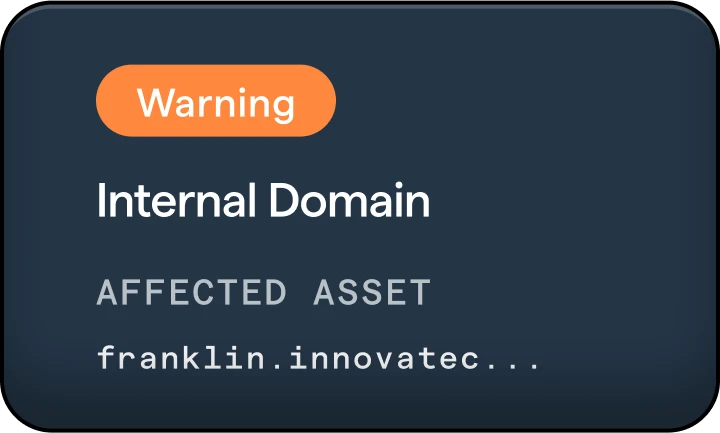
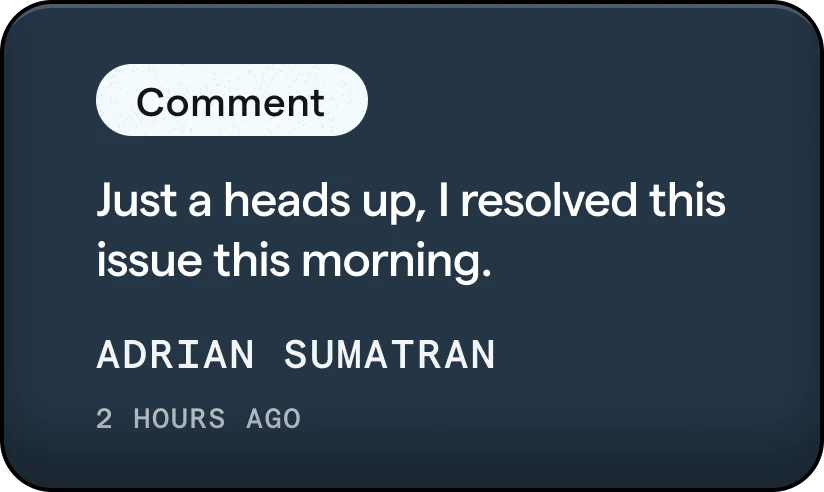

Identity Hub
Get superior protection against all types of identity threats. With access control and fast response, the Identity Hub gives you the ability to address identification incidents and respond to issues as they arise.
See identity hub



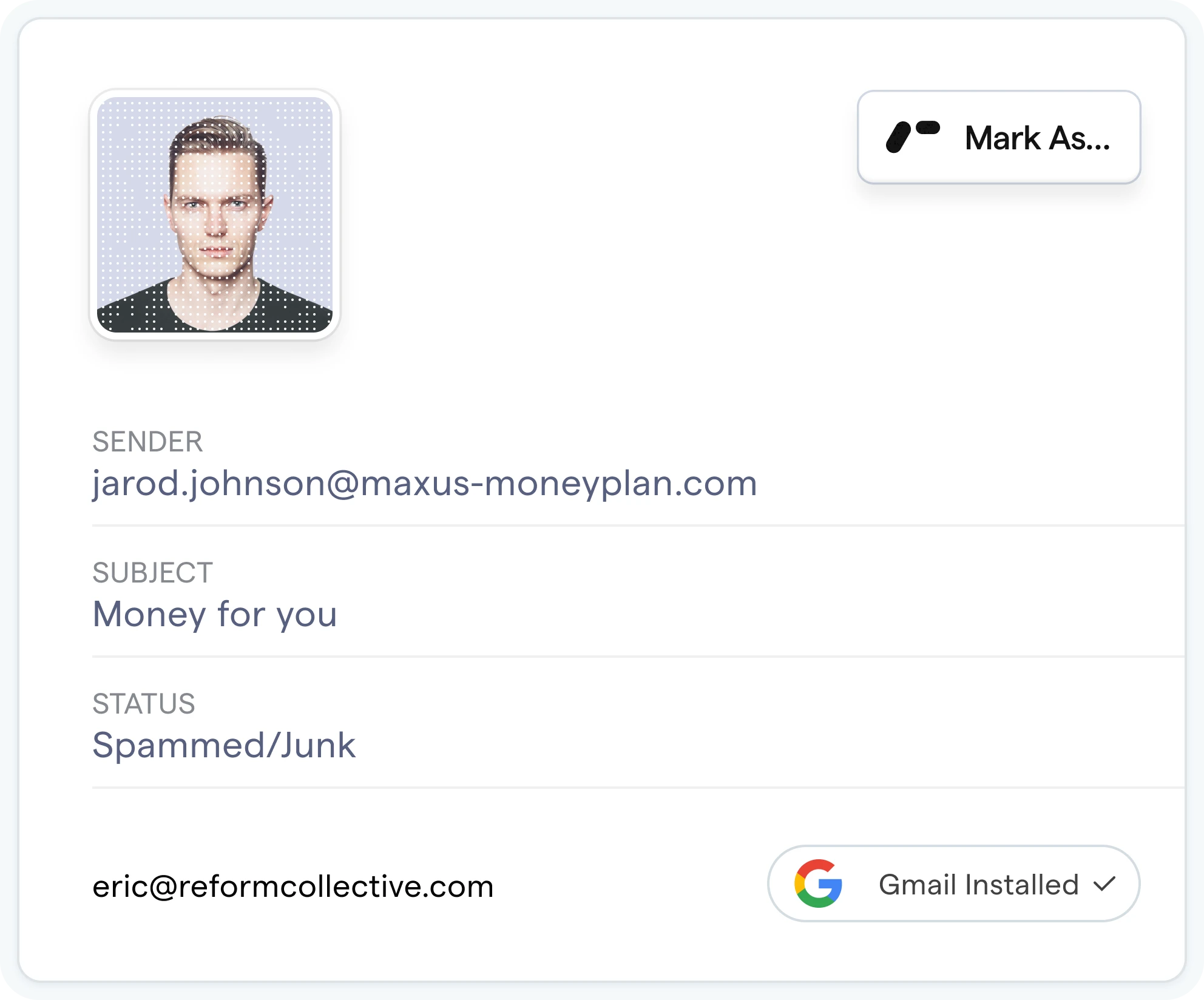
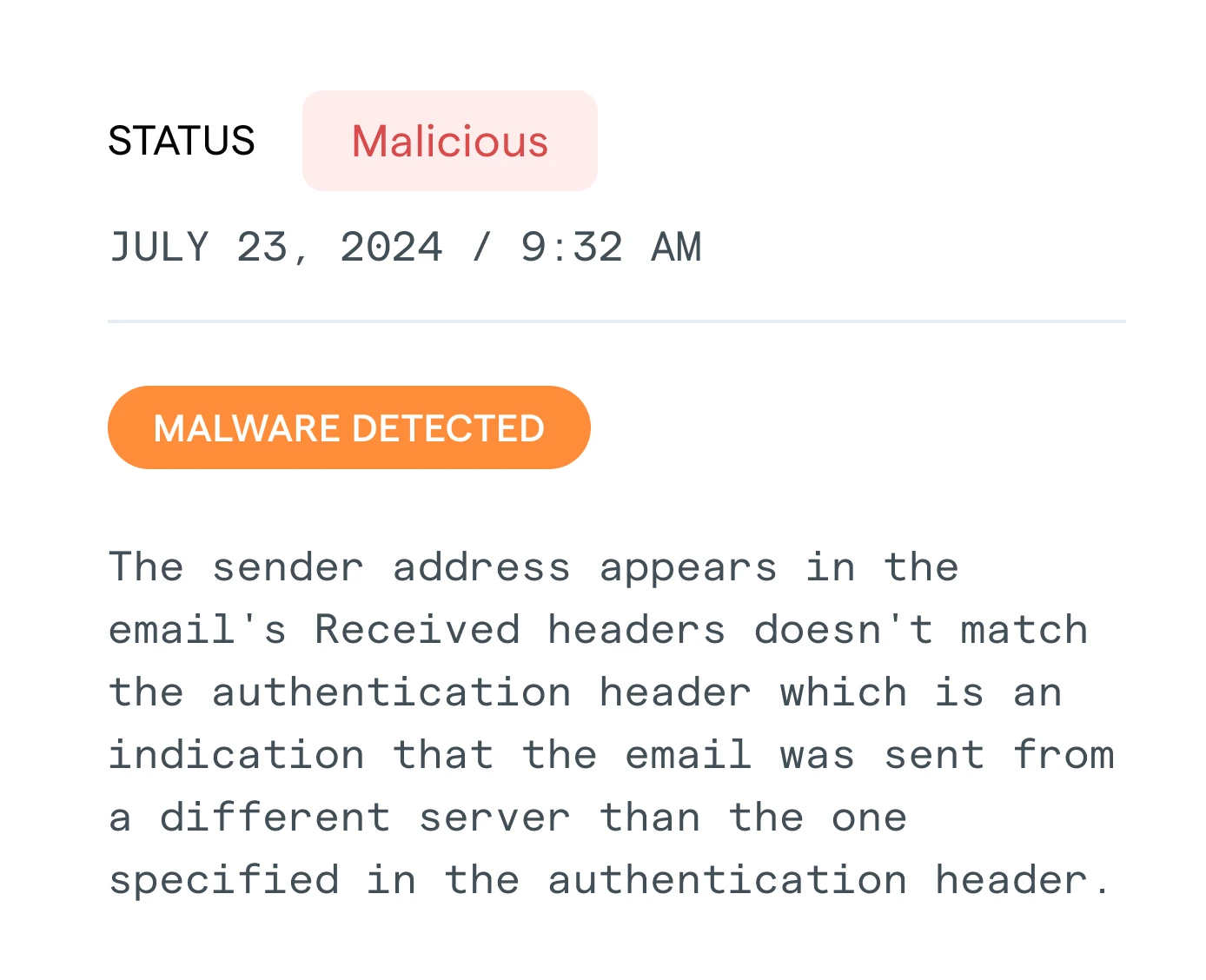
Email Hub
Email can expose you to a myriad of dangers, including phishing frauds, BEC attacks, ATO, spam, fraud, and more. Email Hub gives you peace of mind with the most advanced protection against common swindles.
See Email Hub

Endpoint Hub
Device protection is the keystone of cybersecurity protection. Malware, ransomware, and other threats often enter systems through company equipment. Endpoint Hub secures devices by providing full-fleet observability and ensuring compliance.
See Endpoint Hub

Training Hub
A chain is only as strong as its weakest link, and the right training can strengthen all elements of an organization against cyber threats. The Training Hub provides targeted training modules and individualized performance reports.
See Training Hub

EASM Hub
Strong cybersecurity requires constant vigilance against lurking and opportunistic threats. That’s why EASM Hub acts as an always-on defense that keeps your guard up constantly, giving you visibility across your attack surface and high precision intelligence to ensure the most critical issues are resolved.
See EASM Hub
The power of integration
Any cybersecurity solution needs to be integrated seamlessly with the apps that power today’s organizations. That’s why Rotate’s solutions leverage integrations with major platforms and essential applications.
Get centralized control of cybersecurity
Rotate’s 360-degree solution includes a Partner Portal, which serves as a centralized control center that empowers you with seamless multi-tenancy management capabilities. With Partner Portal you have unprecedented visibility over all your clients’ operations with a single, unified interface.




